Since Windows Server 2008, we can use Group Policy Preferences to set a password for Local Administrator on all workstations in an OU. In May 2014, Microsoft released a patch to remove this feature. KB2962486
In fact, the password was stored insecurely. It was crypted using a key which is now public MSDN. This is a security leak, password are sent in “clear” and several time by day, using GPO application. If KB2928120 is installed on your system, you can’t no more use GPO to define password for:
- Drive Maps.
- Local Users.
- Scheduled Tasks.
- Services.
- Data Sources.
With the Security patch, Microsoft provided a Powershell script to change local password remotely.
Since few days, Microsoft released a new tool: Local Administrator Password Solution (LAPS). With this tool, computers are able to randomly change password for local administrator and store it in Active Directory attribute.
To setup Local Administrator Password Solution, we need to do 6 steps:
- Install Management Server.
- Modify Active Directory to create attributes.
- Set User rights.
- Install LAPS agent on workstations.
- Create GPO to define Password Policy.
- Check data and user rights.
Management Server
Management server provide several tools to manage password information: Powershell cmdlet, GUI to recover password and GPO template.
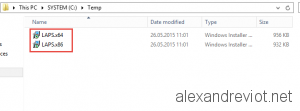
- Download LAPS binaries (x64 and x86) files from Microsoft:
- On the Management Server, start LAPS.x64.msi:
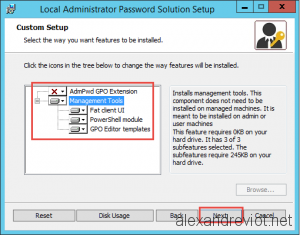
- Select Management Tools features and finish the installation:
- Now, you have the LAPS GUI:
Active Directory Modification
LAPS Agent will store its password into Active Directory attribute: ms-Mcs-AdmPwd on a Computer object. We need to extend the Schema:
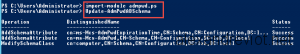
- On the Management Server, start Powershell and Import LAPS Module with Import-module admpwd.ps
- Extend the Schema with the cmdlet Update-AdmPwdADSchema
User Rights
Local Password will be stored in ms-Mcs-AdmPwd attribute. It means that all users with privileges on the OU can read it.
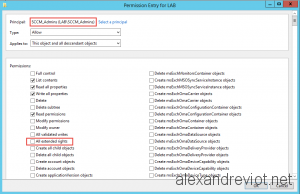
- If you want to remove group to be able to read Password, remove All extended rights. For exemple, SCCM_Admins group will not have the right to read Local Password:
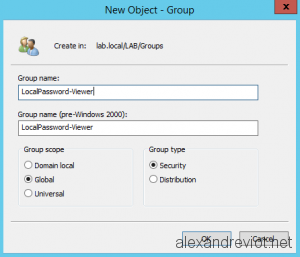
- We need to create an Active Directory group which contains all granted users:
- Read rights for the new group on specific OU with cmdlet Set-AdmPwdReadPasswordPermission -OrgUnit “OU_DN” -AllowedPrincipals “Group”
- Reset rights for the new group on specific OU with cmdlet Set-AdmPwdResetPasswordPermission -OrgUnit “OU_DN” -AllowedPrincipals “Group”
- Allow computer object to set Password on itself with Set-AdmPwdComputerSelfPermission -OrgUnit “OU_DN” :
- You can check effective rights with the cmdlet Find-AdmPwdExtendedrights -identity :”OU_DN” | fl
LAPS Agent
Depend on your system, you need to install x64 or x86 msi file. You can deploy it with SCCM, GPO, or something else.
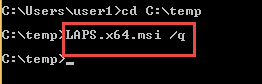
- The installation of the Agent is simple: LAPS.x64.msi /q
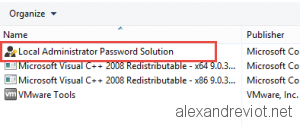
- To check if the software is installed. go to Add Remove Program:
GPO Password Policy
LAPS Agent will get its information from Group Policy. When we installed the Management Server, we also imported template for GPO.
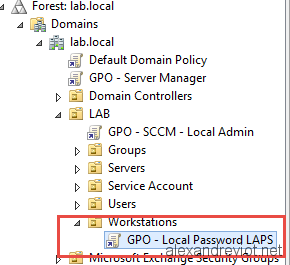
- On the management server, create a GPO under the Workstation’s OU:
- Specify your criteria
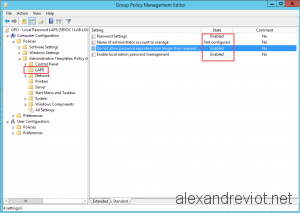
- Path: Computer/Policies/Administrative Templates/LAPS.
- Enable Local Admin Password Management: Enabled.
- Password Setting: Enabled. You can chosse password complexity, length, …
- Do not allow password expiration time longer than required: Enabled.
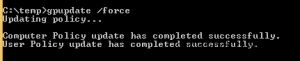
- On your client, force a gpupdate:
Verification
Once the computer finished its gpupdate, it will change its local admin password and send it to Active Directory.
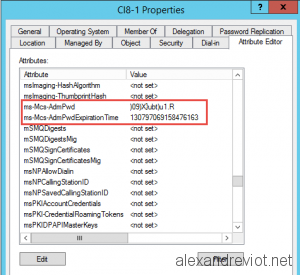
- You can check the information in Active Directory User and Computer, on the computer object, ms-Mcs-AdmPwd:
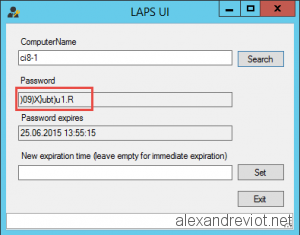
- If you start LAPS UI with a granted user:
- With Powershell, the cmdlet Get-AdmPwdPassword -ComputerName computerName
Congratulation, you successfully set up Local Administrator Password Solution from Microsoft. 🙂
More
You could get more information about LAPS here.

That insight solves the prbolem. Thanks!